Set up Snowflake OAuth EnterpriseEnterprise +
We're migrating dbt platform multi-tenant accounts worldwide to static subdomains. After the migration, you’ll be automatically redirected from your original URL (for example, cloud.getdbt.com) to the new URL static subdomain (for example, abc123.us1.dbt.com), which you can find in your account settings. If your organization has network allow listing, add the us1.dbt.com domain to your allow list.
The migration may require additional actions in your Snowflake account. See subdomain migration for more information.
dbt Enterprise and Enterprise+ supports OAuth authentication with Snowflake. When Snowflake OAuth is enabled, users can authorize their Development credentials using Single Sign On (SSO) via Snowflake rather than submitting a username and password to dbt. If Snowflake is set up with SSO through a third-party identity provider, developers can use this method to log into Snowflake and authorize the dbt Development credentials without any additional setup.
Users connecting to Snowflake using Snowflake OAuth over an AWS PrivateLink connection from dbt will also require access to a PrivateLink endpoint from their local workstation. Where possible, use Snowflake External OAuth instead to bypass this limitation.
From the Snowflake docs:
Currently, for any given Snowflake account, SSO works with only one account URL at a time: either the public account URL or the URL associated with the private connectivity service
To set up Snowflake OAuth in dbt, admins from both are required for the following steps:
- Locate the redirect URI value in dbt.
- Create a security integration in Snowflake.
- Configure a connection in dbt.
To use Snowflake in the Studio IDE, all developers must authenticate with Snowflake in their profile credentials.
Locate the redirect URI value
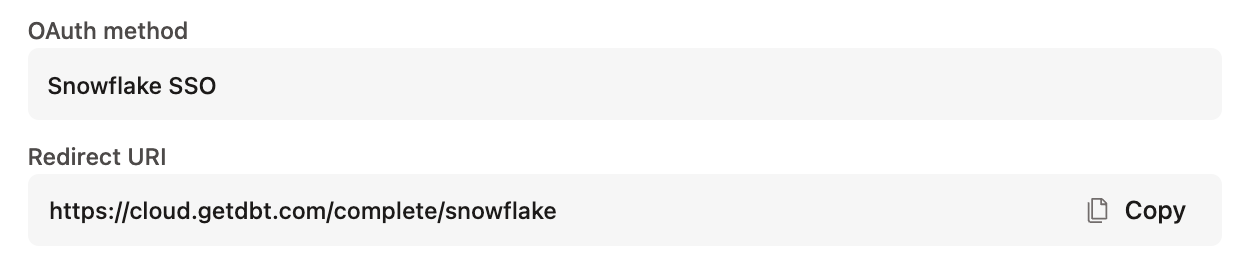
To get started, copy the connection's redirect URI from dbt:
- Navigate to Account settings.
- Select Projects and choose a project from the list.
- Click the Development connection field to view its details and set the OAuth method to "Snowflake SSO".
- Copy the Redirect URI to use in the later steps.
Create a security integration
In Snowflake, execute a query to create a security integration. Please find the complete documentation on creating a security integration for custom clients here.
In the following CREATE OR REPLACE SECURITY INTEGRATION example query, replace <REDIRECT_URI> value with the Redirect URI (also referred to as the access URL) copied in dbt. To locate the Redirect URI, refer to the previous locate the redirect URI value section.
Important: If you’re using secondary roles, you must include OAUTH_USE_SECONDARY_ROLES = 'IMPLICIT'; in the statement.
CREATE OR REPLACE SECURITY INTEGRATION DBT_CLOUD
TYPE = OAUTH
ENABLED = TRUE
OAUTH_CLIENT = CUSTOM
OAUTH_CLIENT_TYPE = 'CONFIDENTIAL'
OAUTH_REDIRECT_URI = '<REDIRECT_URI>'
OAUTH_ISSUE_REFRESH_TOKENS = TRUE
OAUTH_REFRESH_TOKEN_VALIDITY = 7776000
OAUTH_USE_SECONDARY_ROLES = 'IMPLICIT'; -- Required for secondary roles
Note: Only Snowflake account administrators (users with the ACCOUNTADMIN role) or a role with the global CREATE INTEGRATION privilege can execute this SQL command.
| Field | Description |
|---|---|
| TYPE | Required |
| ENABLED | Required |
| OAUTH_CLIENT | Required |
| OAUTH_CLIENT_TYPE | Required |
| OAUTH_REDIRECT_URI | Required. Use the value in the dbt account settings. |
| OAUTH_ISSUE_REFRESH_TOKENS | Required |
| OAUTH_REFRESH_TOKEN_VALIDITY | Required. This configuration dictates the number of seconds that a refresh token is valid for. Use a smaller value to force users to re-authenticate with Snowflake more frequently. |
Additional configuration options may be specified for the security integration as needed.
Configure a Connection in dbt
The Database Admin is responsible for creating a Snowflake Connection in dbt. This Connection is configured using a Snowflake Client ID and Client Secret. These values can be determined by running the following query in Snowflake:
with
integration_secrets as (
select parse_json(system$show_oauth_client_secrets('DBT_CLOUD')) as secrets
)
select
secrets:"OAUTH_CLIENT_ID"::string as client_id,
secrets:"OAUTH_CLIENT_SECRET"::string as client_secret
from
integration_secrets;
To complete the creation of your connection in dbt:
- Navigate to your Account Settings, click Connections, and select a connection.
- Edit the connection and enter the Client ID and Client Secret.
- Click Save.
Authorize developer credentials
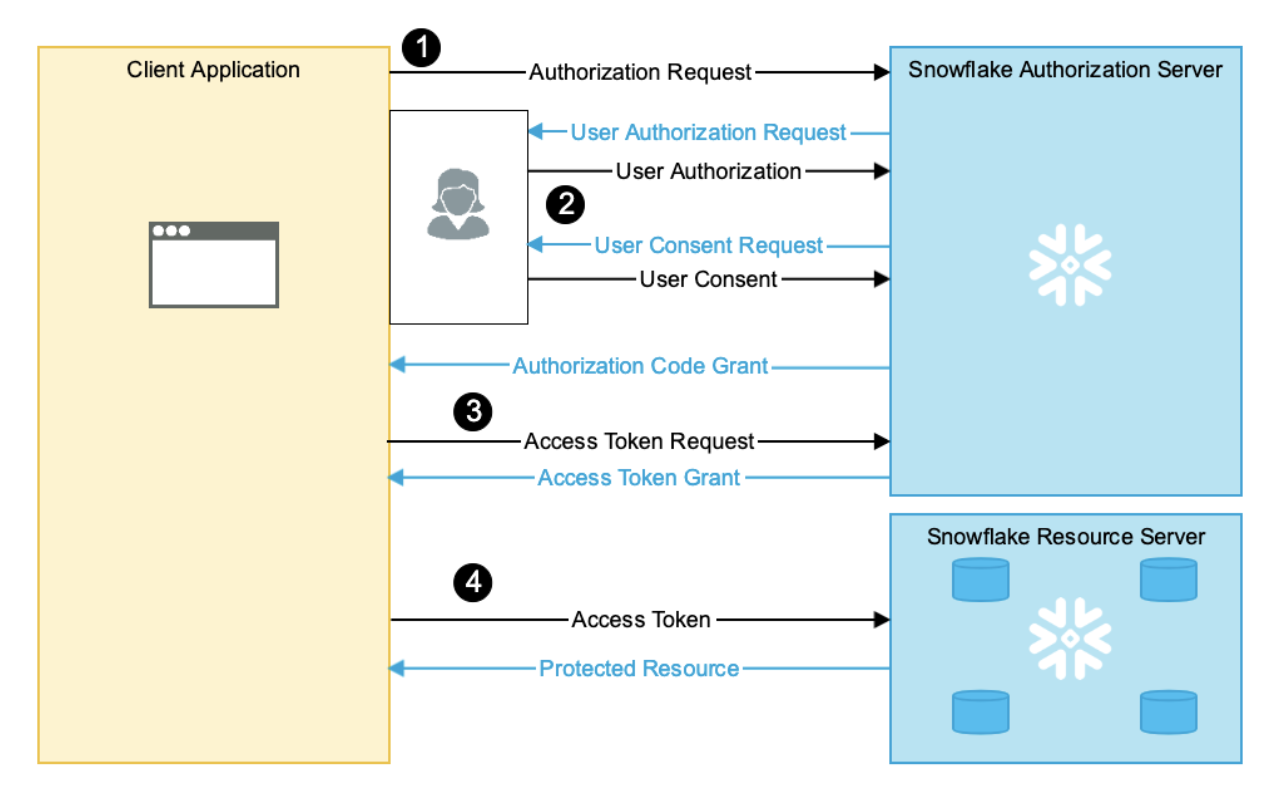
Once Snowflake SSO is enabled, users on the project will be able to configure their credentials in their Profiles. By clicking the "Connect to Snowflake Account" button, users will be redirected to Snowflake to authorize with the configured SSO provider, then back to dbt to complete the setup process. At this point, users should now be able to use the Studio IDE with their development credentials.
SSO OAuth flow diagram
Once a user has authorized dbt with Snowflake via their identity provider, Snowflake will return a Refresh Token to the dbt application. dbt is then able to exchange this refresh token for an Access Token which can then be used to open a Snowflake connection and execute queries in the Studio IDE on behalf of users.
NOTE: The lifetime of the refresh token is dictated by the OAUTH_REFRESH_TOKEN_VALIDITY parameter supplied in the “create security integration” statement. When a user’s refresh token expires, the user will need to re-authorize with Snowflake to continue development in dbt.
Setting up multiple dbt projects with Snowflake 0Auth
If you are planning to set up the same Snowflake account to different dbt projects, you can use the same security integration for all of the projects.
Subdomain migration
If you're a multi-tenant account being migrated to a static subdomain, you may need to take additional action in your Snowflake account to prevent service disruptions.
Snowflake limits each security integration (CREATE SECURITY INTEGRATION … TYPE = OAUTH) to a single redirect URI. If you configured your OAuth integration with cloud.getdbt.com, you must take one of two courses of action:
- Configure an additional security integration: In your Snowflake account, you will have one with the original URL (for example,
cloud.getdbt.com/complete/snowflake) as the redirect URI, and another using the new static subdomain. Refer to our regions & IP addresses page for a complete list of the original domains in your region (marked as "multi-tenant" on the chart). - Use a single security integration: Create one that uses the new static subdomain as the redirect URI. In this scenario, you must recreate all of your existing connections.
Troubleshooting
Learn more
Was this page helpful?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.