This page covers user groups and access, including:
- User licenses, permissions, and group memberships
- Role-based access controls for projects and environments
- Single sign-on, and secure authentication
For model-specific access and their availability across projects, refer to Model access.
About user access
You can regulate access to dbt by various measures, including licenses, groups, permissions, and role-based access control (RBAC). To understand the possible approaches to user access to dbt features and functionality, you should first know how we approach users and groups.
Users
Individual users in dbt can be people you manually invite or grant access via an external identity provider (IdP), such as Microsoft Entra ID, Okta, or Google Workspace.
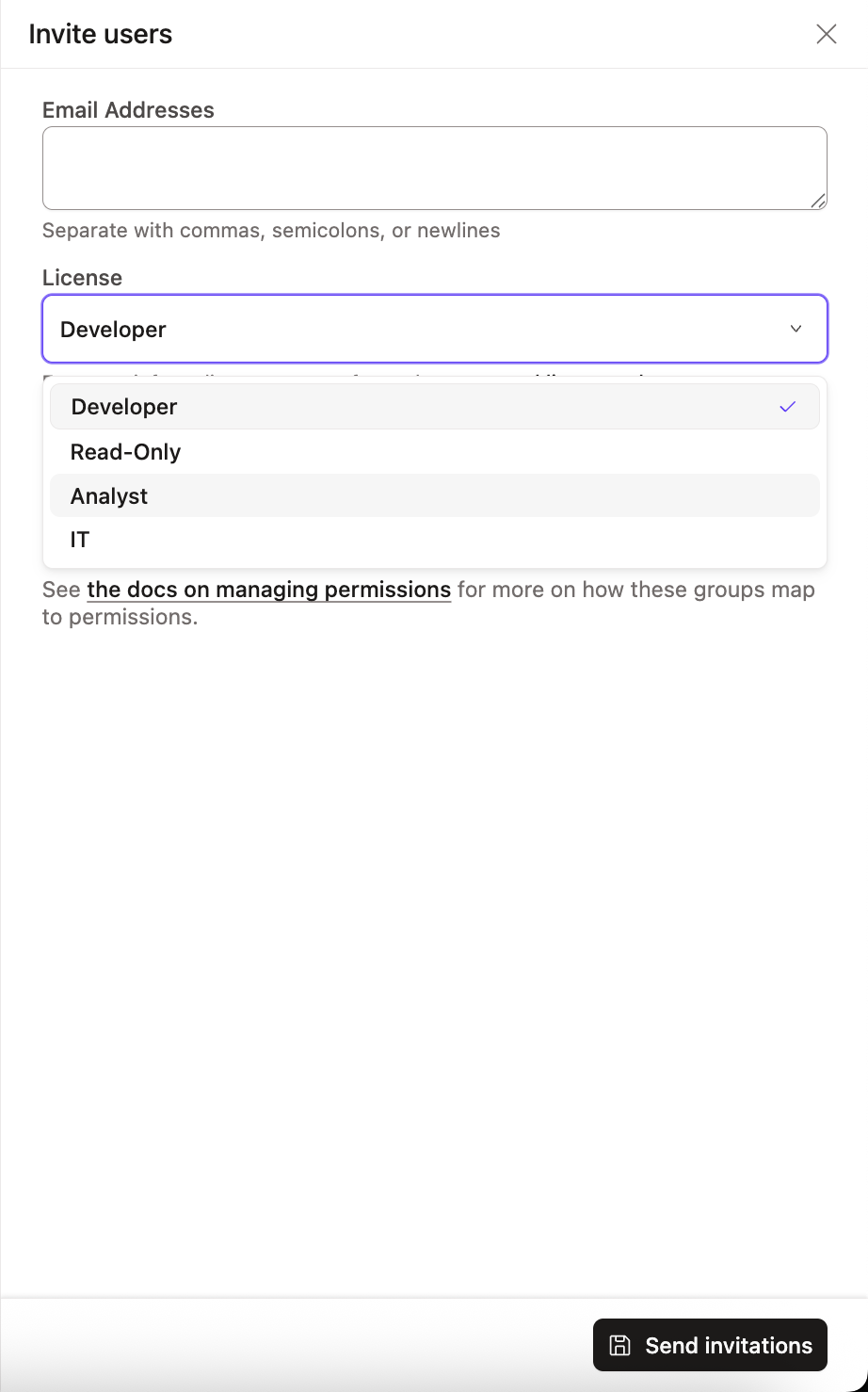
In either scenario, when you add a user to dbt, they are assigned a license. You assign licenses at the individual user or group levels. When you manually invite a user, you will assign the license in the invitation window.
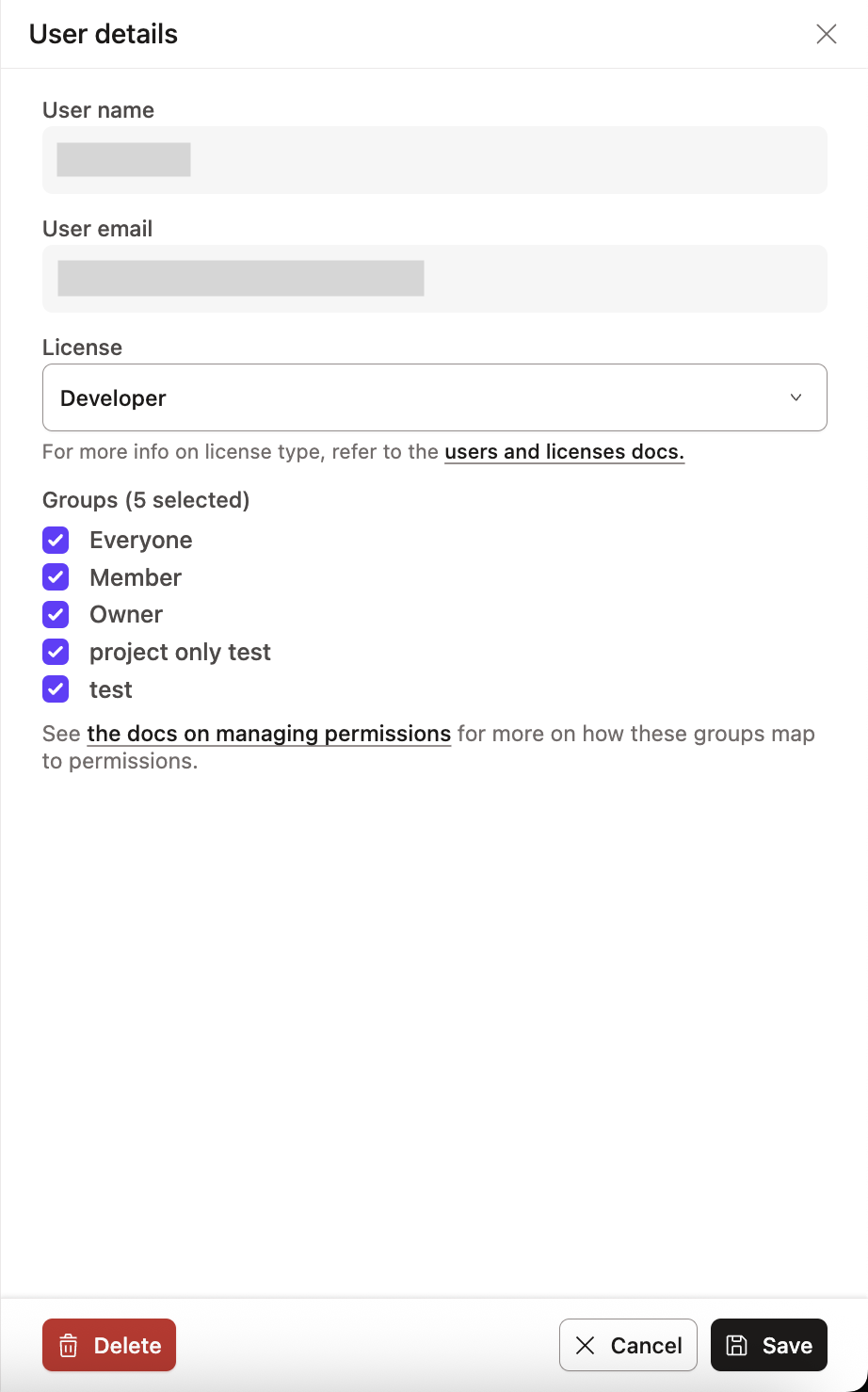
You can edit an existing user's license by navigating to the Users section of the Account settings, clicking on a user, and clicking Edit on the user pane. Delete users from this same window to free up licenses for new users.
User passwords
By default, new users will be prompted to set a password for their account. All plan tiers support and enforce multi-factor authentication for users with password logins. However, they will still need to configure their password before configuring MFA. Enterprise tier accounts can configure SSO and advanced authentication measures. Developer and Starter plans only support user passwords with MFA.
User passwords must meet the following criteria:
- Be at least nine characters in length
- Contain at least one uppercase and one lowercase letter
- Contain at least one number 0-9
- Contain at least one special character
Groups
Groups in dbt serve much of the same purpose as they do in traditional directory tools — to gather individual users together to make bulk assignments of permissions easier.
The permissions available depends on whether you're on an Enterprise-tier or self-service Starter plan.
- Admins use groups in dbt to assign licenses and permissions.
- The permissions are more granular than licenses, and you only assign them at the group level; you can’t assign permissions at the user level.
- Every user in dbt must be assigned to at least one group.
There are three default groups available as soon as you create your dbt account (the person who created the account is added to all three automatically):
- Owner: This group is for individuals responsible for the entire account and will give them elevated account admin privileges. You cannot change the permissions.
- Member: This group is for the general members of your organization. Default permissions are broad, restricting only access to features that can alter billing or security. By default, dbt adds new users to this group.
- Everyone: A general group for all members of your organization. Customize the permissions to fit your organizational needs. By default, dbt adds new users to this group.
The Owner and Member groups have default permission sets:
- Starter plan: The
OwnerandMembergroups use theOwnerandMemberpermission sets, respectively. - Enterprise plans: By default, dbt assigns the
Ownergroup anAccount Adminpermission set, and theMembergroup aMemberpermission set, which doesn't appear in the settings, but has the same privileges as theAdminpermission set.
Default groups are automatically provisioned for all accounts to simplify the initial set up. We recommend creating your own organizational groups so you can customize the permissions. Once you create your own groups, you can delete the default groups.
Create new groups EnterpriseEnterprise +
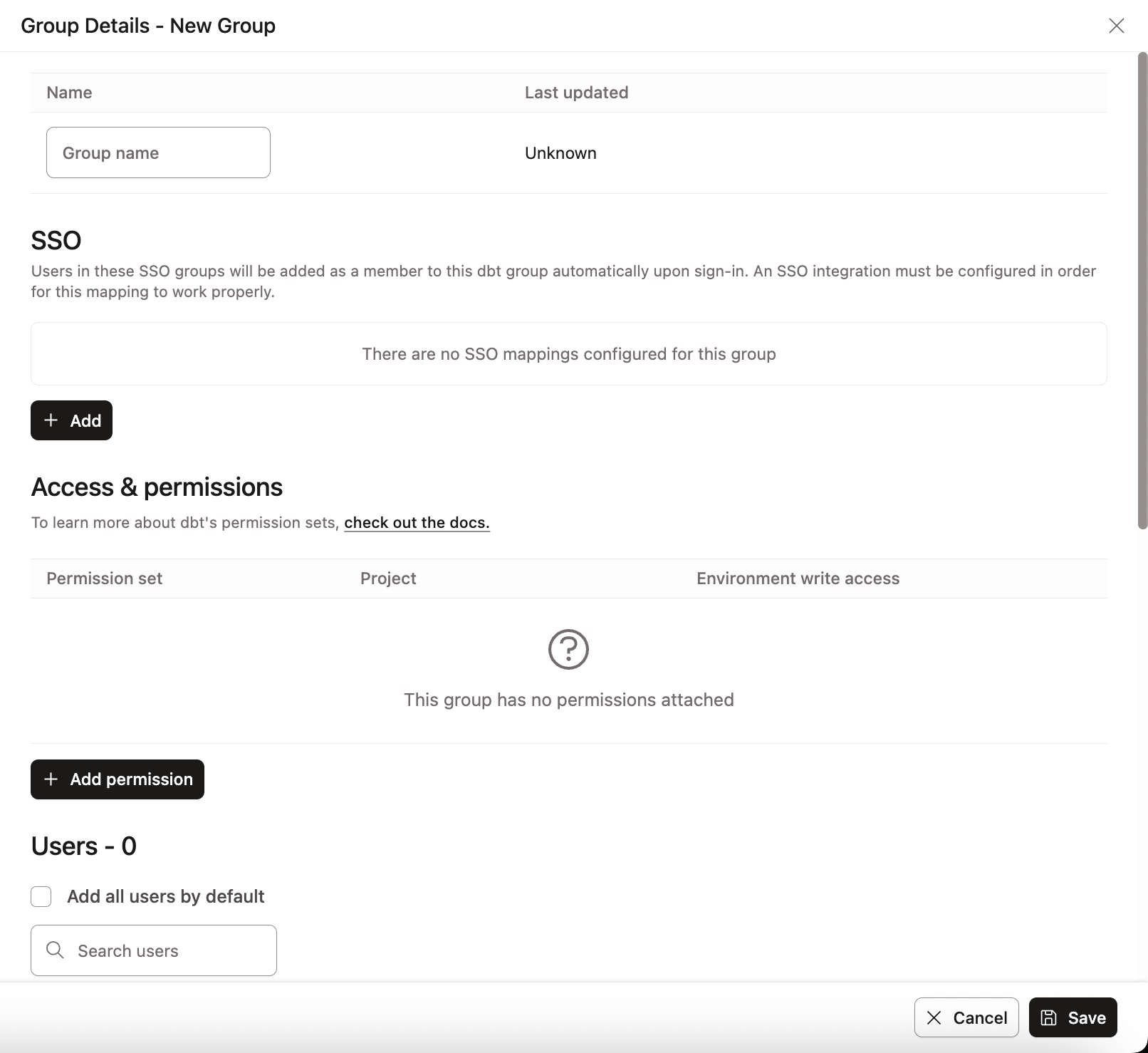
- Create new groups from the Groups & Licenses section of the Account settings.
- If you use an external IdP for SSO, you can sync those SSO groups to dbt from the Group details pane when creating or editing existing groups.
If a user is assigned licenses and permissions from multiple groups, the group that grants the most access will take precedence. You must assign a permission set to any groups created beyond the three defaults, or users assigned will not have access to features beyond their user profile.
Group access and permissions
The Access & Permissions section of a group is where you can assign users the right level of access based on their role or responsibilities. You decide:
- Projects the group can access
- Roles that the group members are assigned for each
- Environments the group can edit
This setup provides you with the flexibility to determine the level of access users in any given group will have. For example, you might allow one group of analysts to edit jobs in their project, but only let them view related projects, or you could grant admin-level access to a team that owns a specific project while keeping others restricted to read-only.
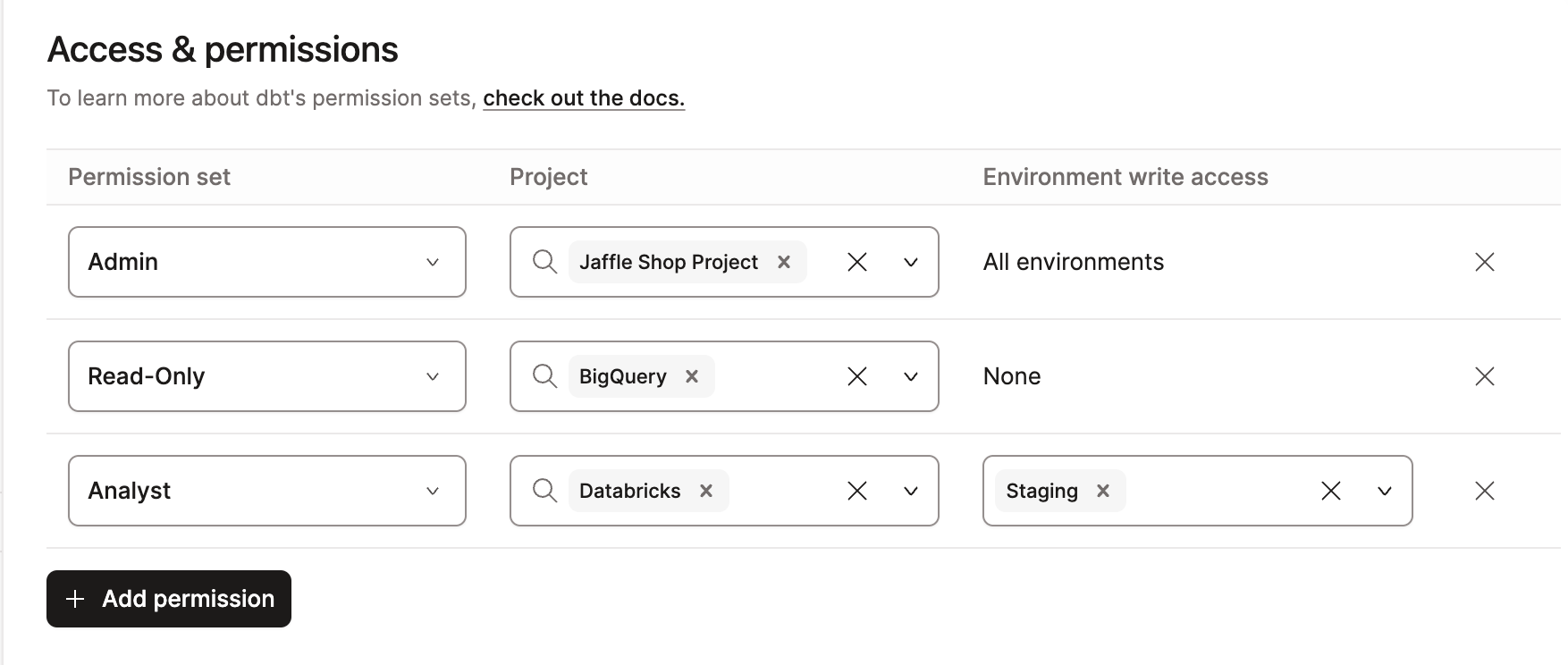
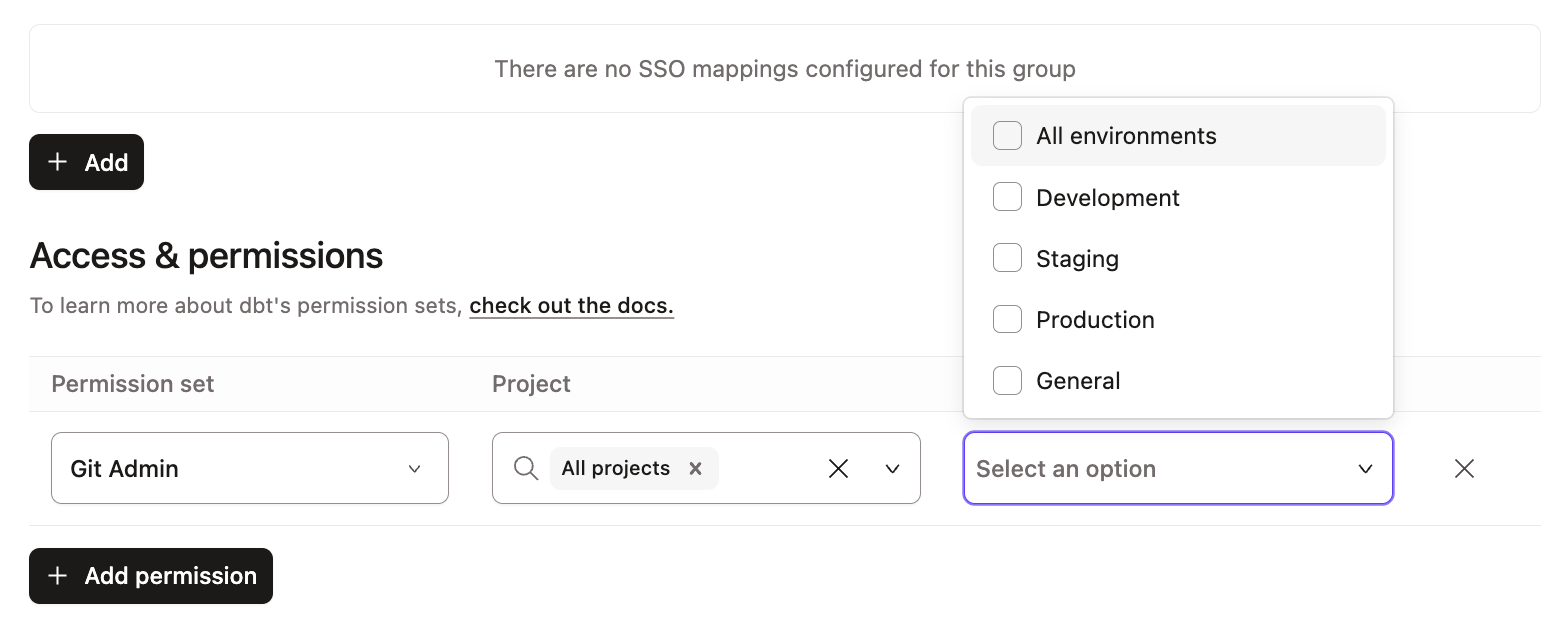
Environment write access
Some permission sets grant users read-only access to environment settings that can be overridden if you assign them to a group with Environment write access. They will then be able to create, edit, and delete environment settings such as jobs and runs, bypassing the read-only restriction. This elevated access doesn't grant users the ability to create or delete environments.
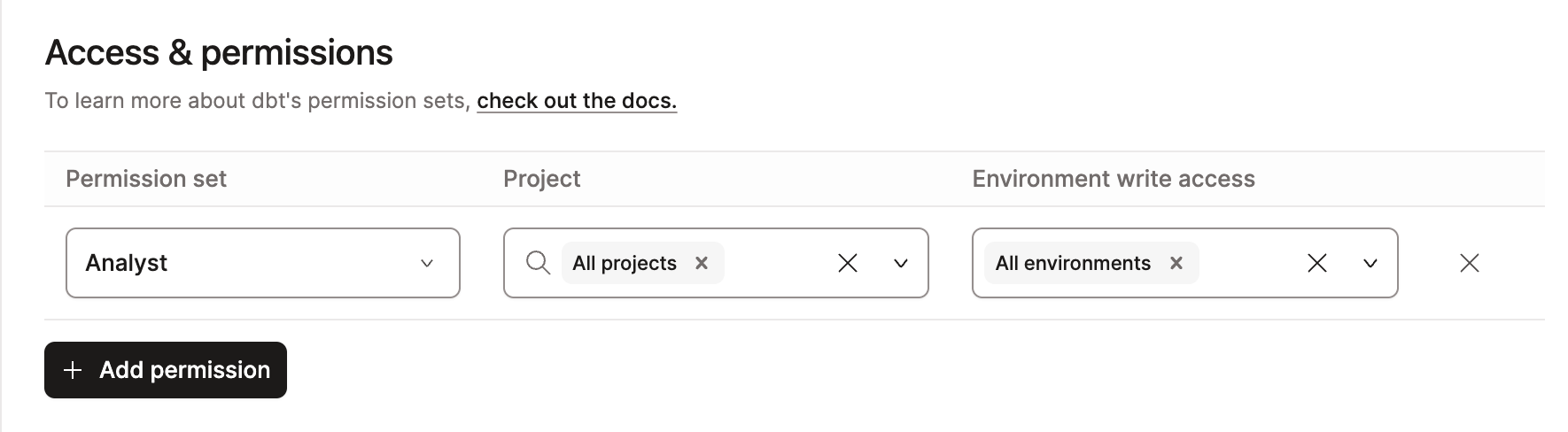
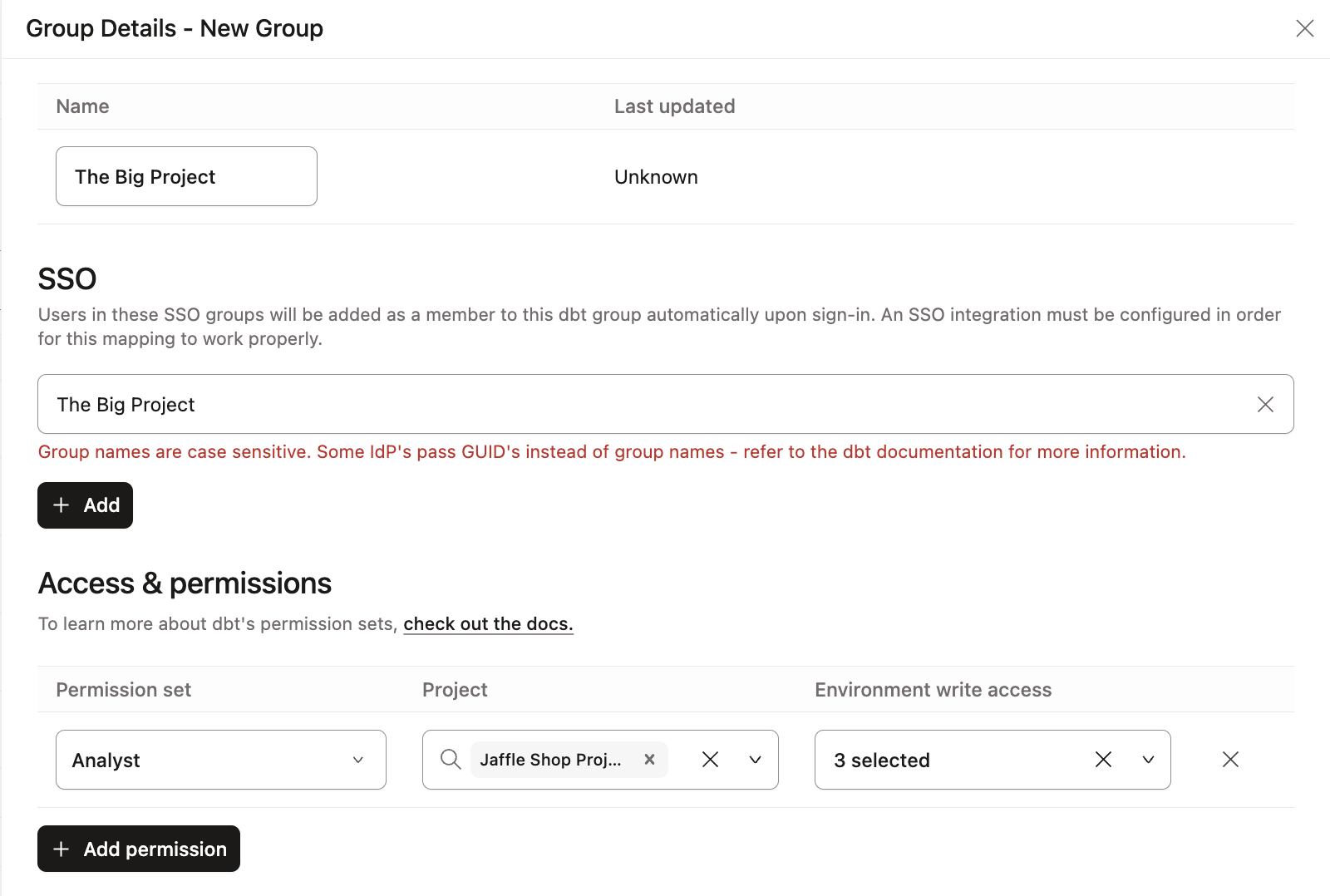
In the following example, the analyst permission set, which by default has read-only access to jobs, is assigned to the group across all projects; however, the Environment write access is set to All Environments. This grants all users in this group the ability to create, edit, and delete jobs across all environments and projects.
Only use Environment write access settings when you intend to grant users the ability to edit environments. To grant users only the permissions inherent to their set, leave this setting blank (all boxes unchecked).
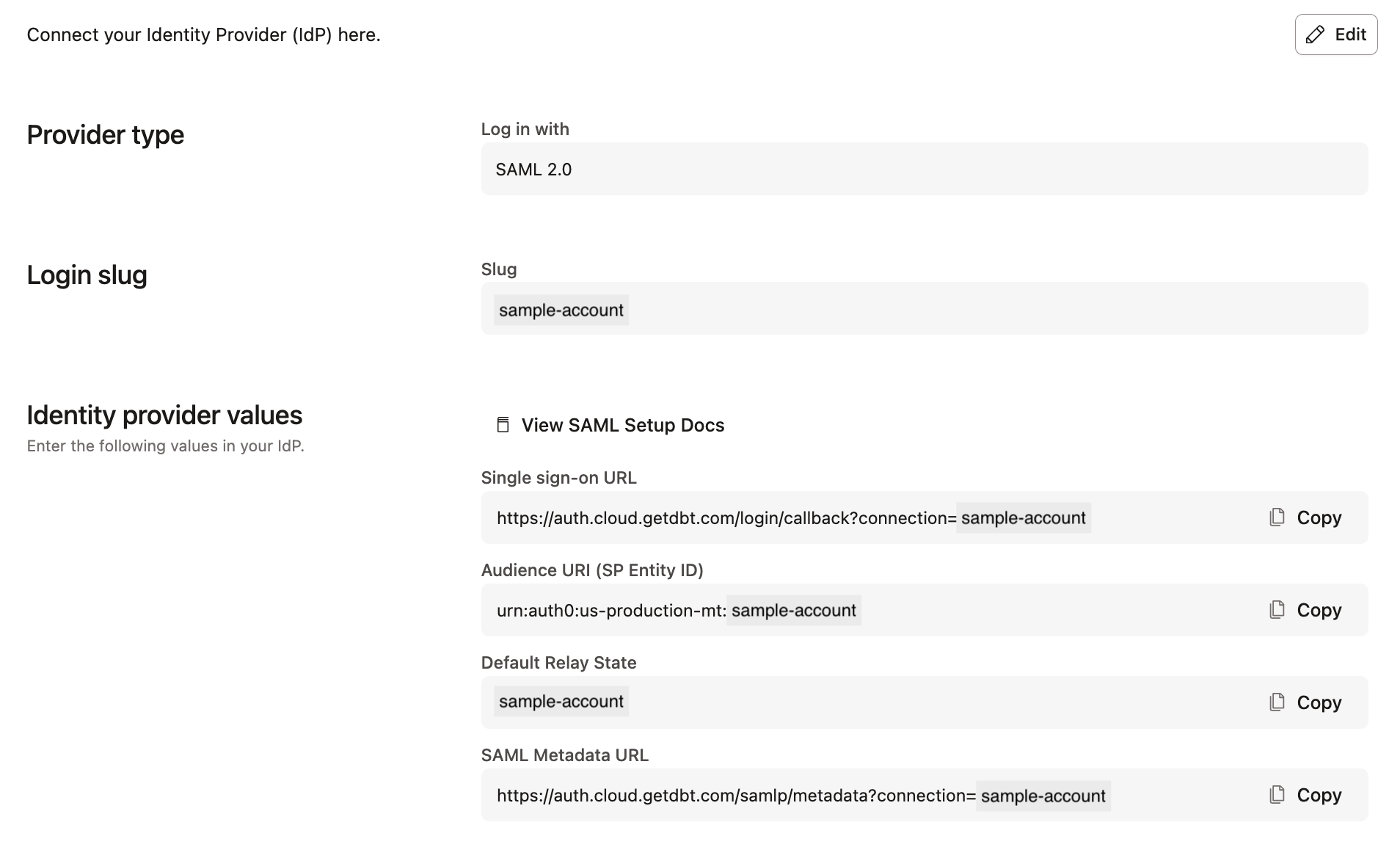
SSO mappings EnterpriseEnterprise +
SSO Mappings connect an identity provider (IdP) group membership to a dbt group. When users log into dbt via a supported identity provider, their IdP group memberships sync with dbt. Upon logging in successfully, the user's group memberships (and permissions) will automatically adjust within dbt.
While dbt supports mapping multiple IdP groups to a single dbt group, we recommend using a 1:1 mapping to make administration as simple as possible. Use the same names for your dbt groups and your IdP groups.
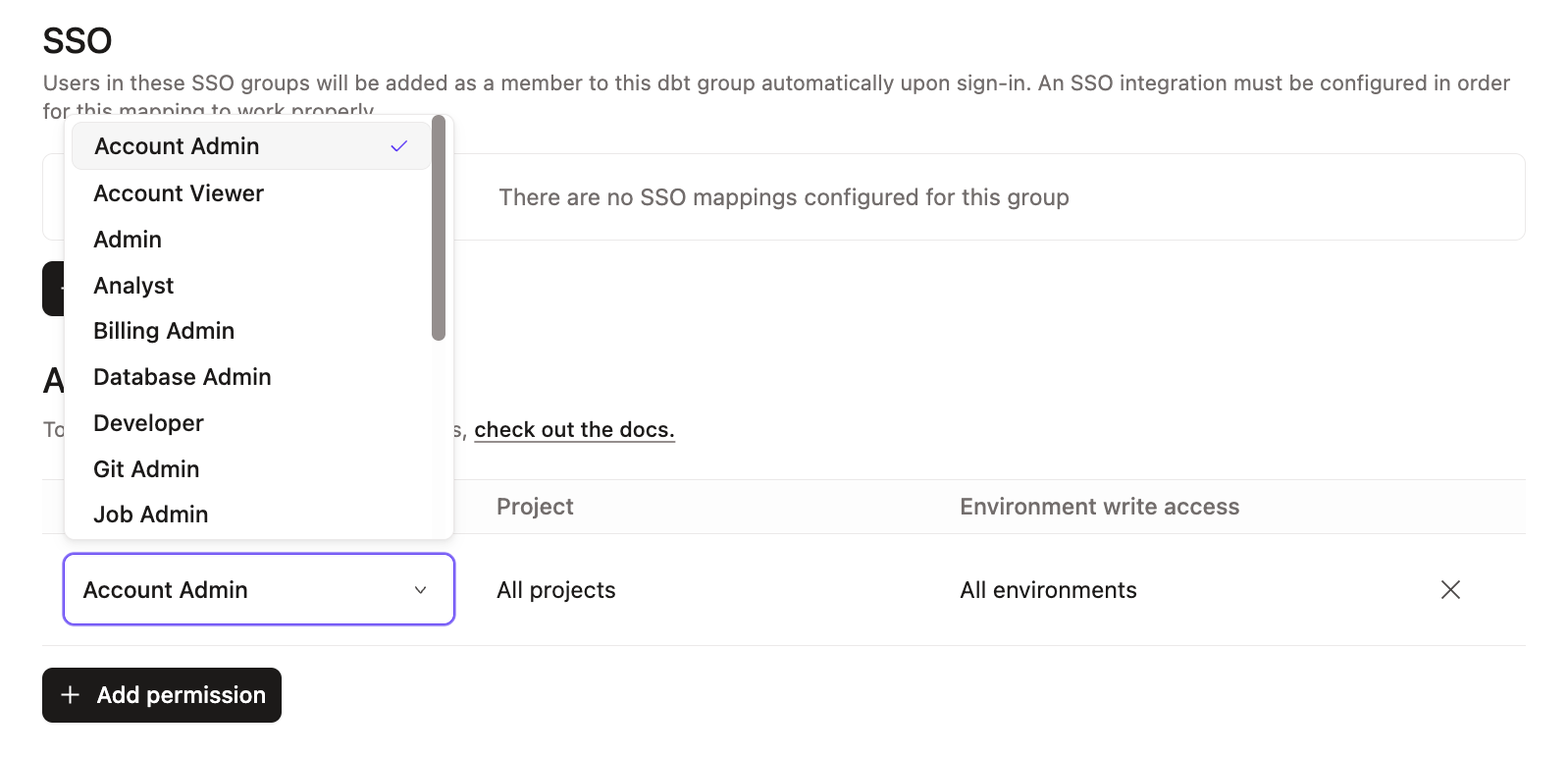
Create an SSO mapping in the group view:
- Open an existing group to edit or create a new group.
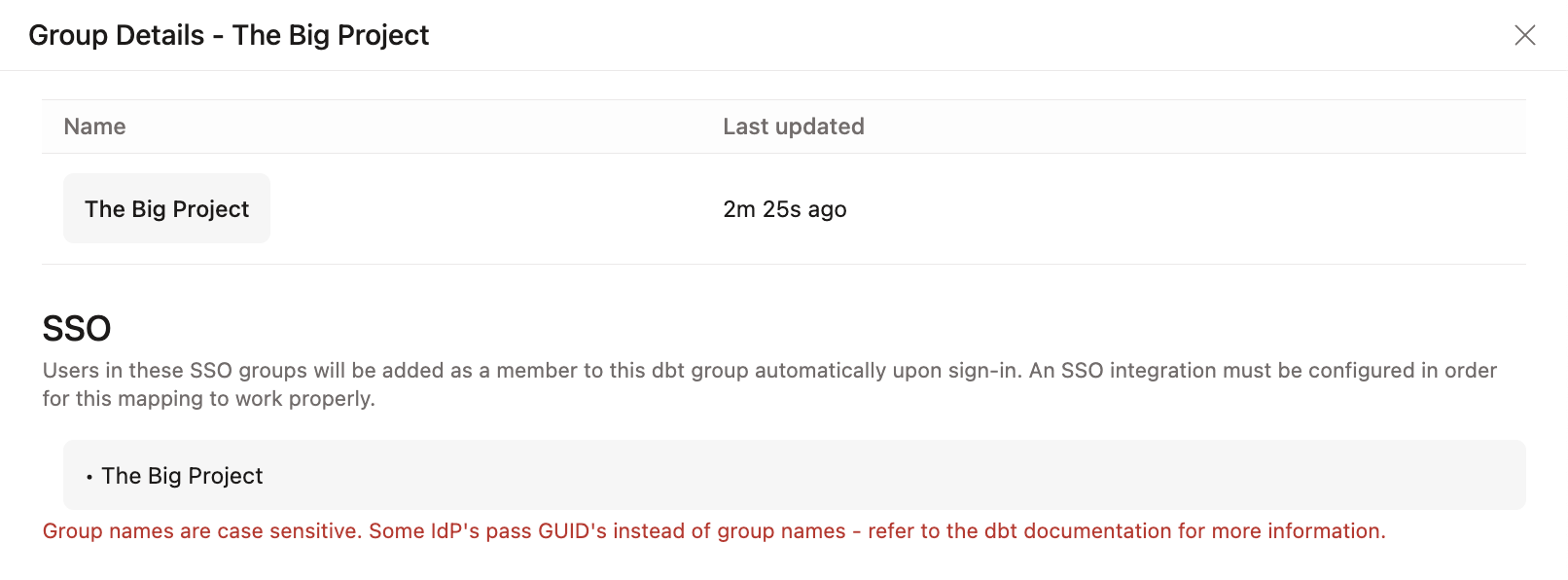
- In the SSO portion of the group screen, enter the name of the SSO group exactly as it appears in the IdP. If the name is not the same, the users will not be properly placed into the group.
- In the Users section, ensure the Add all users by default option is disabled.
- Save the group configuration. New SSO users will be added to the group upon login, and existing users will be added to the group upon their next login.
Refer to role-based access control for more information about mapping SSO groups for user assignment to dbt groups.
Grant access
dbt users have both a license (assigned to an individual user or by group membership) and permissions (by group membership only) that determine what actions they can take. Licenses are account-wide, and permissions provide more granular access or restrictions to specific features.
Licenses
Every user in dbt will have a license assigned. Licenses consume "seats" which impact how your account is billed, depending on your service plan.
There are four license types in dbt:
- Analyst — Available on Enterprise and Enterprise+ plans only. Requires developer seat license purchase.
- User can be granted any permission sets.
- Developer — User can be granted any permission sets.
- IT — Available on Starter, Enterprise, and Enterprise+ plans only. User has Security Admin and Billing Admin permissions applied.
- Can manage users, groups, connections, and licenses, among other permissions.
- IT licensed users do not inherit rights from any permission sets.
- Every IT licensed user has the same access across the account, regardless of the group permissions assigned.
- Read-Only — Available on Starter, Enterprise, and Enterprise+ plans only.
- User has read-only permissions applied to all dbt resources.
- Intended to view the artifacts and the deploy section (jobs, runs, schedules) in a dbt account, but can’t make changes.
- Read-only licensed users do not inherit rights from any permission sets.
- Every read-only licensed user has the same access across the account, regardless of the group permissions assigned.
Developer licenses will make up a majority of the users in your environment and have the highest impact on billing, so it's important to monitor how many you have at any given time.
For more information on these license types, see Seats & Users
User license types always override their assigned group permission sets. For example, a user with a Read-Only license cannot perform administrative actions, even if they belong to an Account Admin group.
This ensures that license restrictions are always enforced, regardless of group membership.
Permissions
Permissions determine what a developer-licensed user can do in your dbt account. By default, members of the Owner and Member groups have full access to all areas and features. When you want to restrict access to features, assign users to groups with stricter permission sets. Keep in mind that if a user belongs to multiple groups, the most permissive group will take precedence.
The permissions available depends on whether you're on an Enterprise, Enterprise+, or self-service Starter plan. Developer accounts only have a single user, so permissions aren't applicable.
Some permissions (those that don't grant full access, like admins) allow groups to be "assigned" to specific projects and environments only. Read about environment-level permissions for more information on restricting environment access.
Role-based access control EnterpriseEnterprise +
Role-based access control (RBAC) allows you to grant users access to features and functionality based on their group membership. With this method, you can grant users varying access levels to different projects and environments. You can take access and security to the next level by integrating dbt with a third-party identity provider (IdP) to grant users access when they authenticate with your SSO or OAuth service.
There are a few things you need to know before you configure RBAC for SSO users:
- New SSO users join any groups with the Add all new users by default option enabled. By default, the
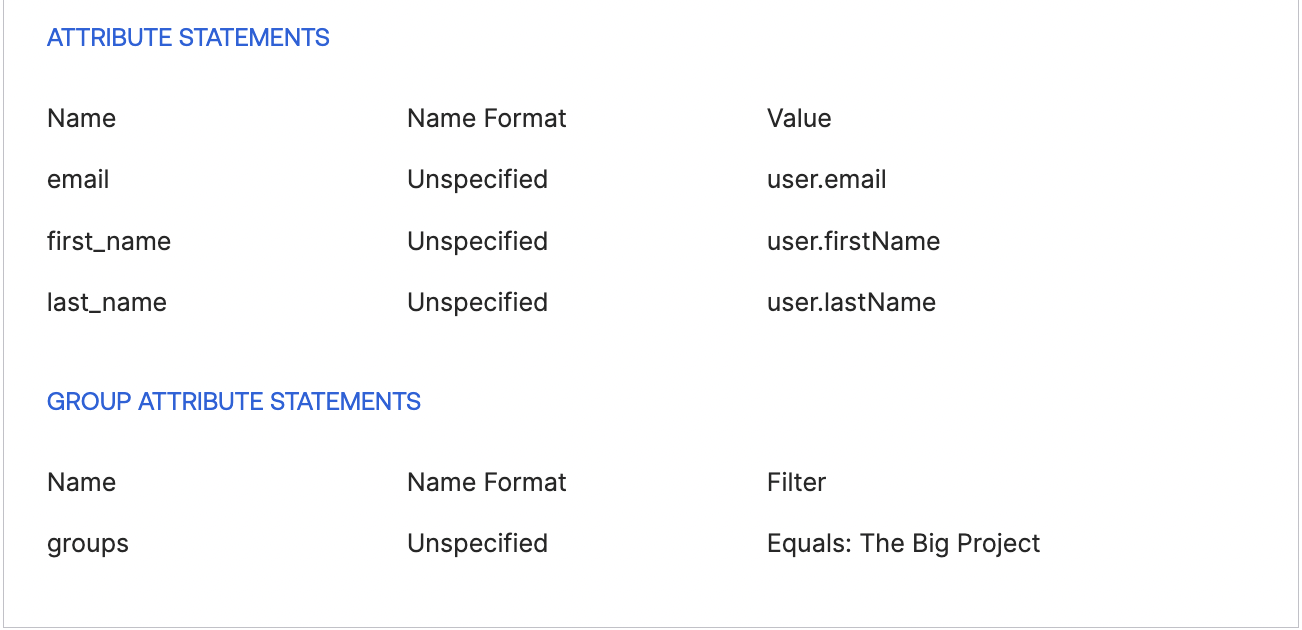
EveryoneandMembergroups have this option enabled. Disable this option across all groups for the best RBAC experience. - You must have the appropriate SSO groups configured in the group details SSO section. If the SSO group name does not match exactly, users will not be placed in the group correctly.
- dbt Labs recommends that your dbt group names match the IdP group names.
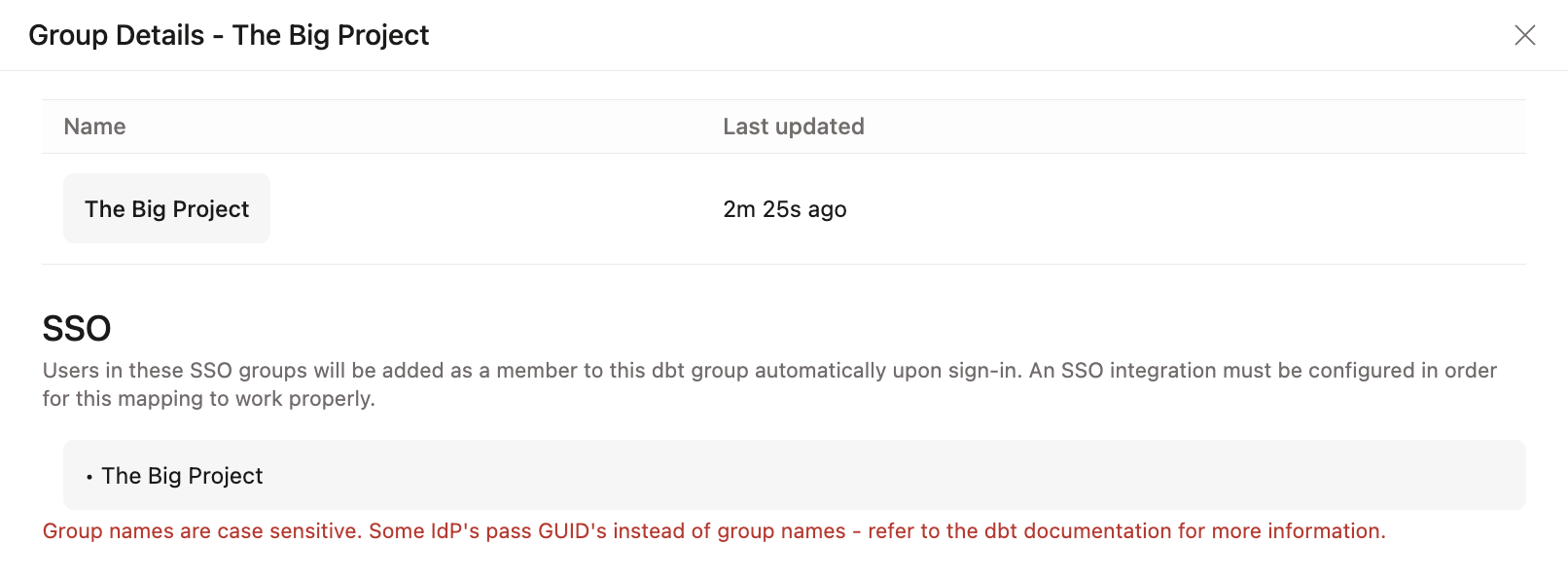
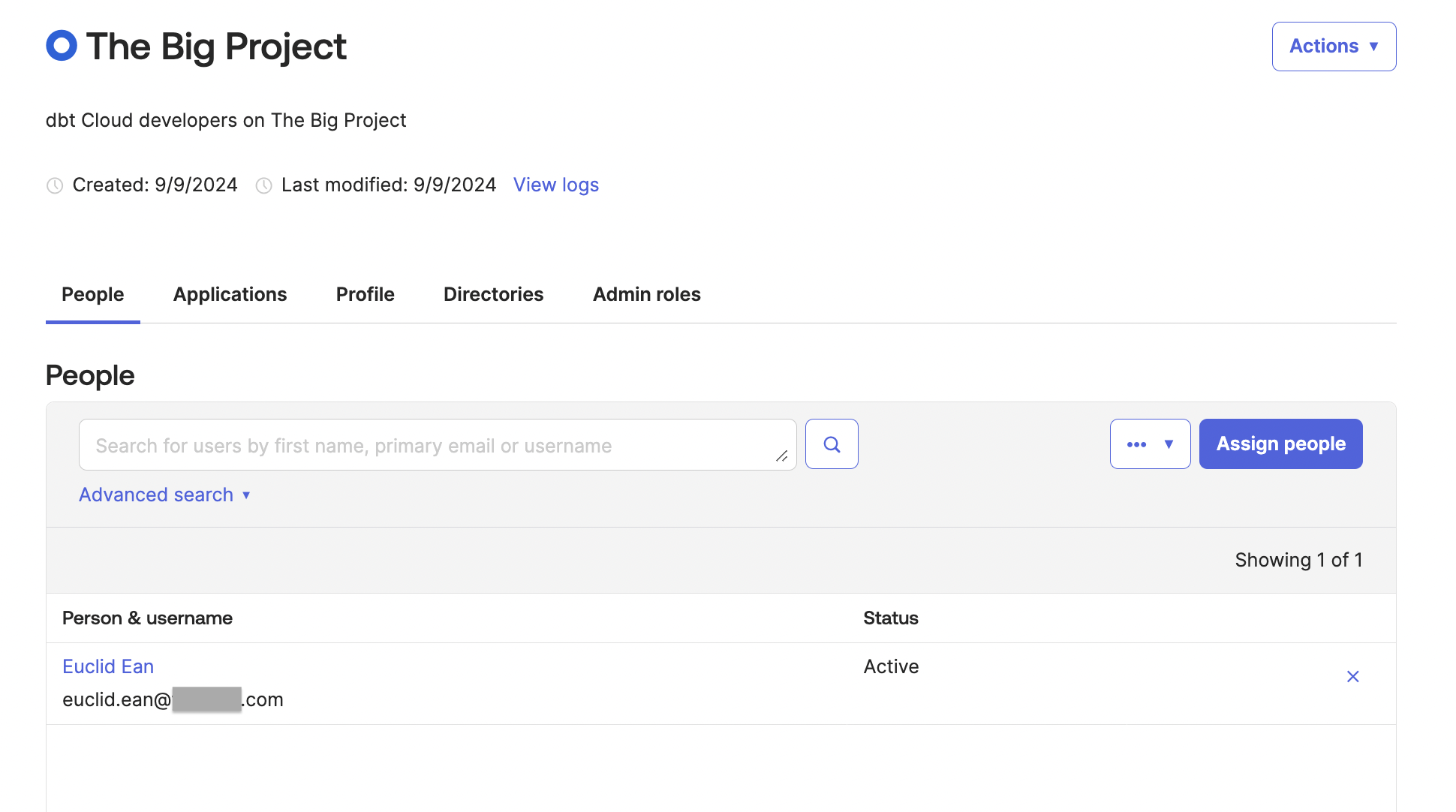
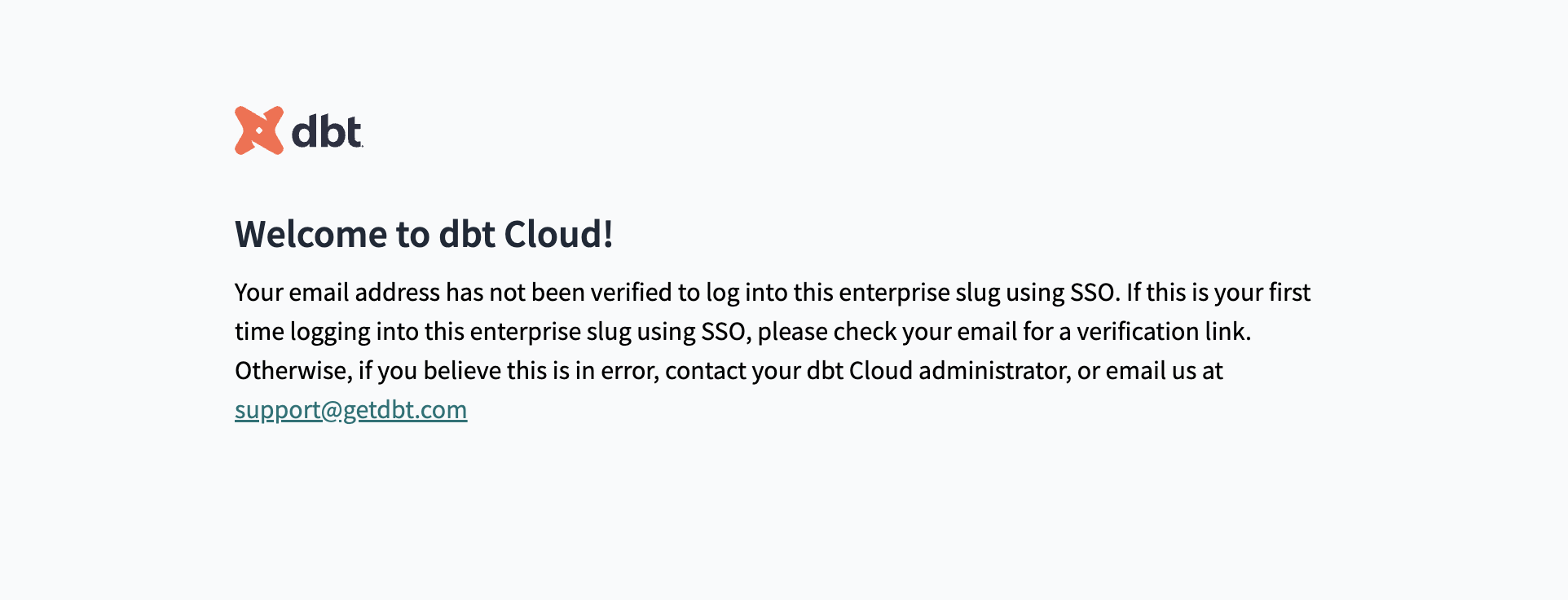
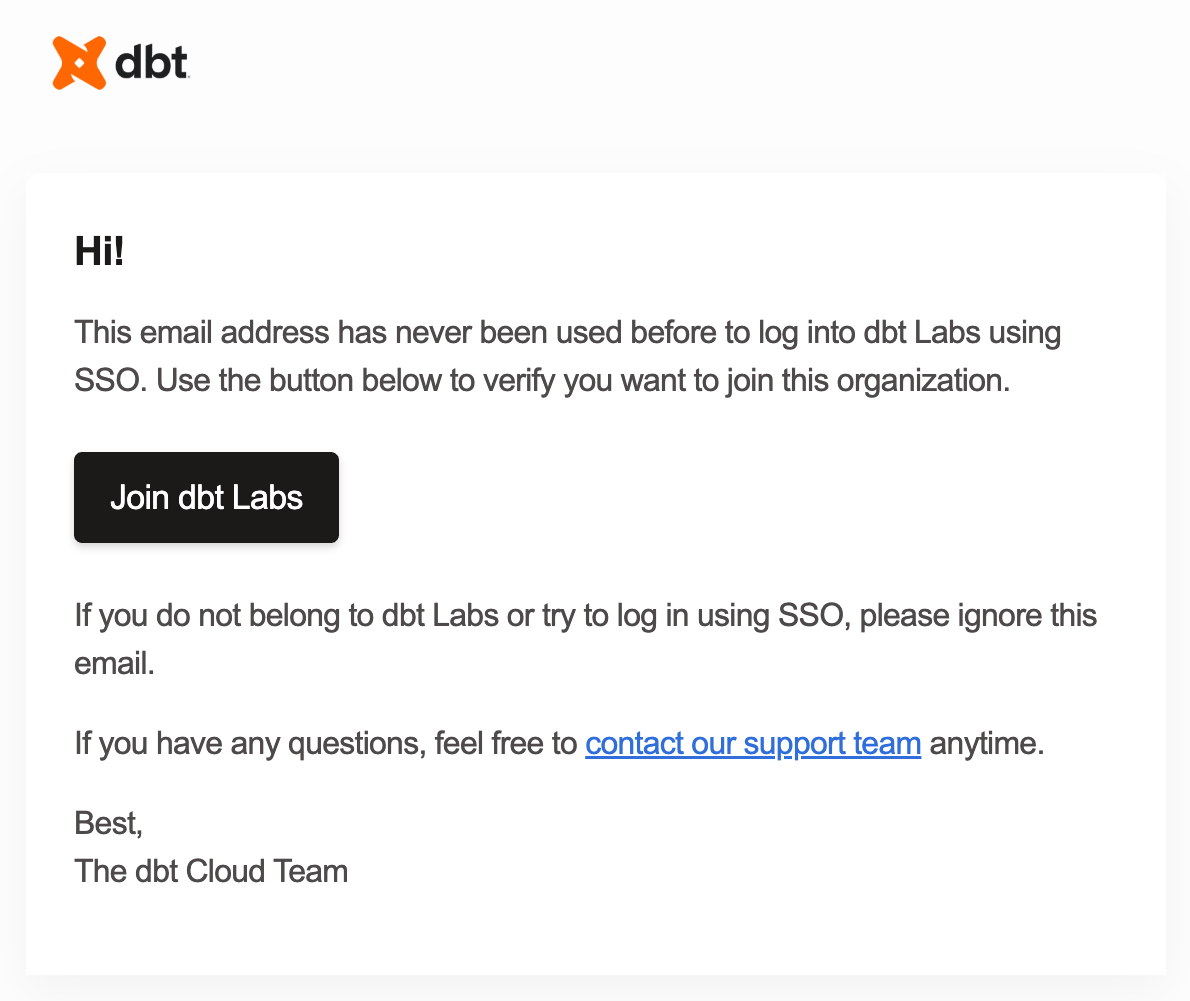
Let's say you have a new employee being onboarded into your organization using Okta as the IdP and dbt groups with SSO mappings. In this scenario, users are working on The Big Project and a new analyst named Euclid Ean is joining the group.
Check out the following example configurations for an idea of how you can implement RBAC for your organization (these examples assume you have already configured SSO):
With RBAC configured, you now have granular control over user access to features across dbt.
SCIM license management
As part of the SSO configuration for supported IdPs, you can also configure the System for Cross-Domain Identity Management (SCIM) settings to add a layer of security to your user lifecycle management. As part of this process, you can integrate user license distribution into the user provisioning process through your IdP. See the SCIM license management instructions for more information.
FAQs
Learn more
Was this page helpful?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.