Connect Redshift Fusion compatible
dbt platform supports connecting to Redshift.
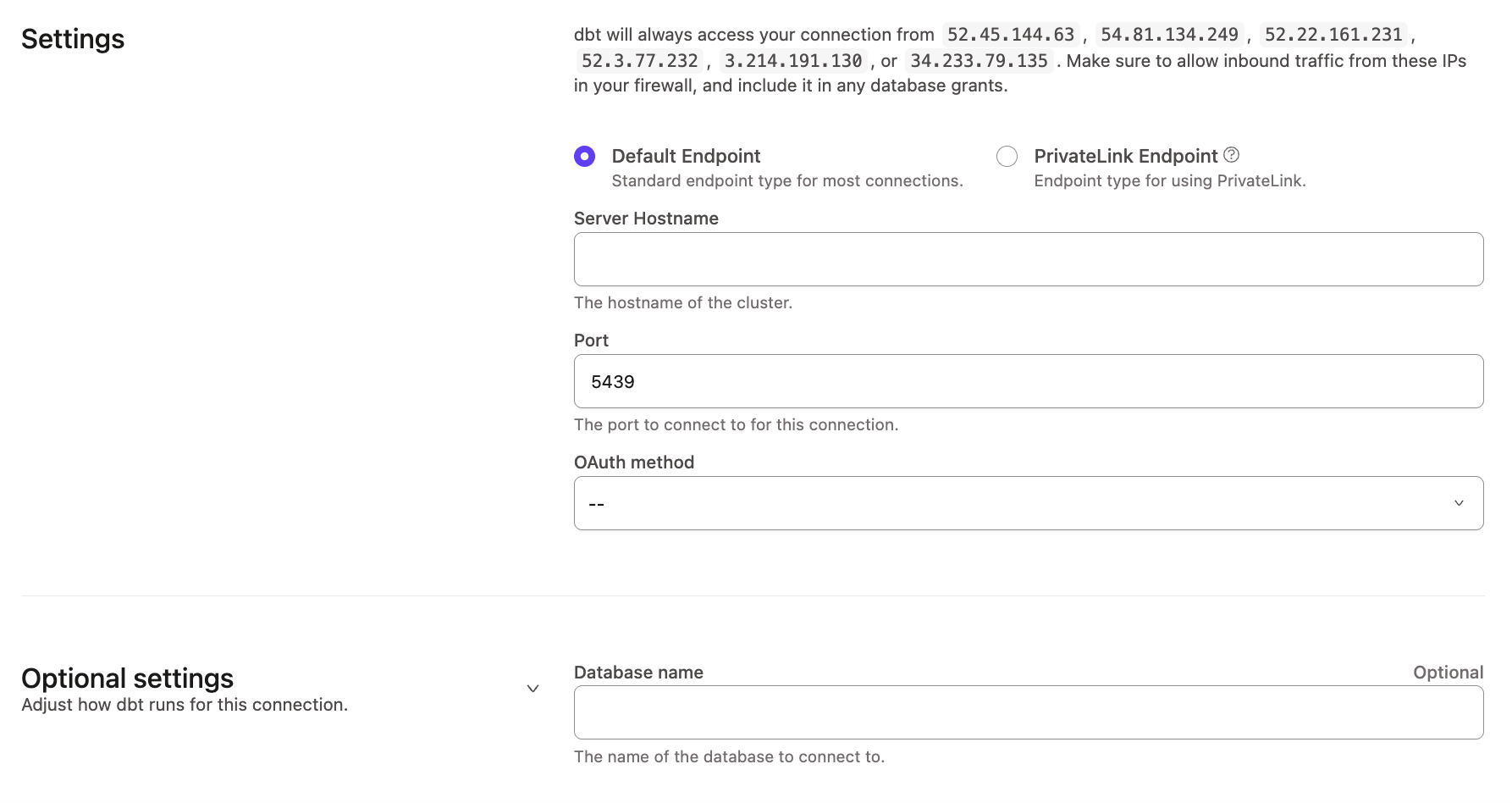
The following fields are required when creating a connection:
| Loading table... |
Note: When you set up a Redshift connection in dbt, SSL-related parameters aren't available as inputs.
Authentication Parameters
See the following supported authentication methods for Redshift:
- Username and password
- SSH tunneling
- Identity Center via external Oauth
- IAM User authentication via extended attributes
On the dbt platform, the IAM user authentication is currently only supported via extended attributes. Once the project is created, development and deployment environments can be updated to use extended attributes to pass the fields described below, as some are not supported via textbox.
You will need to create an IAM User, generate an access key, and either:
- on a cluster, a database user is expected in the
userfield. The IAM user is only leveraged for authentication, the database user for authorization - on Serverless, grant permission to the IAM user in Redshift. The
userfield is ignored (but still required) - For both, the
passwordfield will be ignored.
| Loading table... |
Example Extended Attributes for IAM User on Redshift Serverless
To avoid pasting secrets in extended attributes, leverage environment variables:
host: my-production-instance.myregion.redshift-serverless.amazonaws.com
method: iam
region: us-east-2
access_key_id: '{{ env_var(''DBT_ENV_ACCESS_KEY_ID'') }}'
secret_access_key: '{{ env_var(''DBT_ENV_SECRET_ACCESS_KEY'') }}'
Both DBT_ENV_ACCESS_KEY_ID and DBT_ENV_SECRET_ACCESS_KEY will need to be assigned for every environment leveraging extended attributes as such.
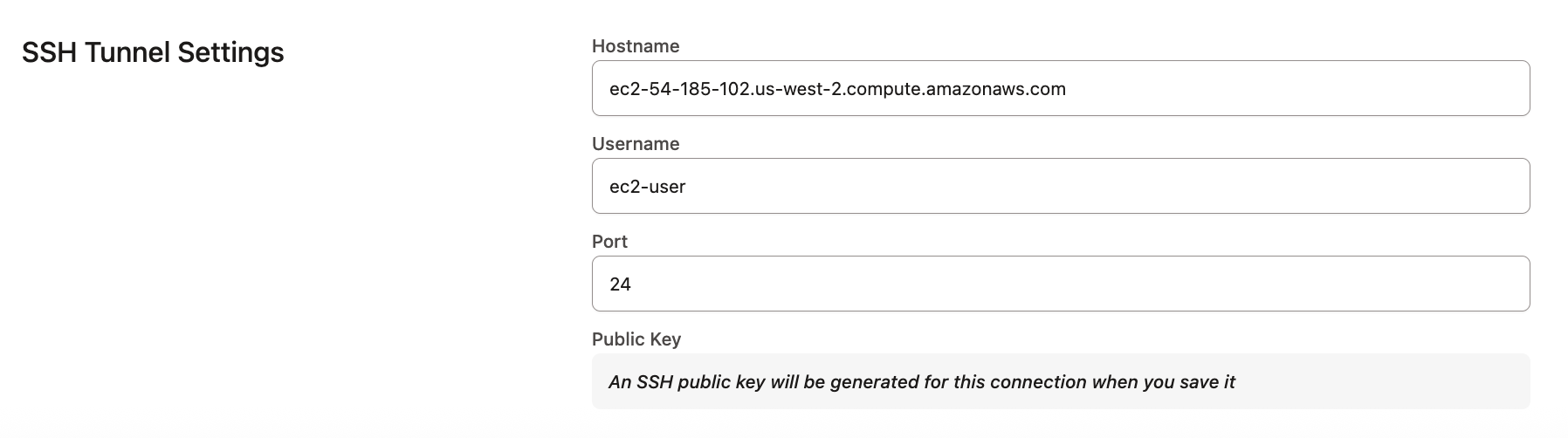
Connecting using an SSH Tunnel
Use an SSH tunnel when your Redshift instance is not publicly accessible and must be reached through a bastion server. When enabled, dbt platform connects to your database by first establishing a secure connection to the bastion host, which then forwards traffic to your database.
To configure a connection using an SSH tunnel:
- Navigate to Account settings (by clicking on your account name in the left side menu) and select Connections.
- Select an existing connection to edit it, or click + New connection.
- In Connection settings, ensure SSH Tunnel Enabled is checked.
- Enter the hostname, username, and port for the bastion server.
-
Click Save. dbt platform generates and displays a public key.
-
Copy the newly generated public key to the bastion server and add it to the server’s
authorized_keysfile to authorize dbt platform to connect through the bastion host. If the new key is not added, the SSH tunnel connection will fail.importantEach time you create and save a new SSH tunnel connection, dbt platform generates a unique SSH key pair, even when the connection details are identical to an existing connection.
About the Bastion server in AWS
What is a bastion server?
A bastion server in Amazon Web Services (AWS) is a host that allows dbt to open an SSH connection.
dbt only sends queries and doesn't transmit large data volumes. This means the bastion server can run on an AWS instance of any size, like a t2.small instance or t2.micro.
Make sure the location of the instance is the same Virtual Private Cloud (VPC) as the Redshift instance, and configure the security group for the bastion server to ensure that it's able to connect to the warehouse port.
Configuring the Bastion Server in AWS
To configure the SSH tunnel in dbt, you'll need to provide the hostname/IP of your bastion server, username, and port, of your choosing, that dbt will connect to. Review the following steps:
-
Verify the bastion server has its network security rules set up to accept connections from the dbt IP addresses on whatever port you configured.
-
Set up the user account by using the bastion servers instance's CLI, The following example uses the username
dbtcloud:sudo groupadd dbtcloud
sudo useradd -m -g dbtcloud dbtcloud
sudo su - dbtcloud
mkdir ~/.ssh
chmod 700 ~/.ssh
touch ~/.ssh/authorized_keys
chmod 600 ~/.ssh/authorized_keys -
Copy and paste the dbt generated public key, into the authorized_keys file.
The bastion server should now be ready for dbt to use as a tunnel into the Redshift environment.
Configuration
To optimize performance with data platform-specific configurations in dbt, refer to Redshift-specific configuration.
To grant users or roles database permissions (access rights and privileges), refer to the Redshift permissions page.
FAQs
Was this page helpful?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.